As mentioned many times before, I constantly rebuild my lab and want to automate as much as possible. This applies to Active Directory Users as well.
Helge Klein has already a great blog post on the topic, Creating Realistic Test User Accounts in Active Directory. If you read the comments you will discover that there’s an awesome service online called Fake Name Generator.
Helge’s script create the users, but the HomeShare and the users HomeFolder is not part of the script. I wanted something that does that as well and comply with Permissions that need to be set to allow automate users home directory creations. I also wanted test files to be copied to the users HomeFolder root.
So I reached out to my PowerShell guru Adam Bertram and today I want to share the result with the Community. Enjoy!
First create the CSV file with the Fake Name Generator, make sure to replace the first line with FirstName,LastName.
Place it wherever and change your Parameters.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 |
#Requires -Version 4 <# .SYNOPSIS This script provisions new Active Directory users and create their home folders .EXAMPLE1 PS> New-MyAdUser.ps1 -UserAccount [pscustomobject]@{'FirstName' = 'Adam'; 'LastName' = 'Bertram'; 'HomeDrive' = 'X'; 'BaseHomeDirectory' = '\\server\homefolders'} This will create the base home folder path (if it doesn't exist), set appropriate NTFS permissions on the folder, create the home folder file share, set appropriate file share permissions, create the user's home folder of 'abertram' in the BaseHomeDirectory folder, set appropriate NTFS permissions and create an enabled Active Directory user with first name of 'Adam', last name of 'Bertram', samAccountName of 'abertram' inside the default Users container with a password of the $DefaultUserPassword parameter and set the home drive to X:. .EXAMPLE2 PS> Import-Csv C:\somecsv.csv | .\New-MyAdUser.ps1 .PARAMETER BaseHomeFolderPath The root folder that will contain all user home folders .PARAMETER UserAccount A hashtable with user account attributes .PARAMETER DefaultUserPassword The password that will be set for each user account .PARAMETER HomeFolderShareName This will be the name of the SMB share that's created for the parent folder for all user home folders .PARAMETER BaseUncHomeFolderPath When the home folder share attribute is assigned to the AD user account this will be the parent folder of the user's share. .PARAMETER TestFilesFolderPath This is the folder that contains any files necessary to be copied to each user's home folder. This script will copy all files in this folder to each user's home folder #> [CmdletBinding()] param ( [Parameter(ValueFromPipeline)] [object[]]$UserAccount, [string]$BaseHomeFolderPath = 'C:\Shares\UserHome', [string]$DefaultUserPassword = 'P@ssw0rd', [string]$HomeDrive = 'H', [string]$HomeFolderShareName = 'UserHome', [string]$BaseUncHomeFolderPath = "\\dc-01.ctxlab.local\$HomeFolderShareName", [string]$TestFilesFolderPath = 'C:\PSAdUsers\Test', [string]$OuLocation = 'OU=Test,OU=Users,OU=Deployment' ) begin { $ErrorActionPreference = [System.Management.Automation.ActionPreference]::Stop Set-StrictMode -Version Latest function Set-MyFileSystemAcl { <# .SYNOPSIS This function allows an easy method to set a file system access ACE .PARAMETER Path The file path of a file .PARAMETER Identity The security principal you'd like to set the ACE to. This should be specified like DOMAIN\user or LOCALMACHINE\User. .PARAMETER Right One of many file system rights. For a list http://msdn.microsoft.com/en-us/library/system.security.accesscontrol.filesystemrights(v=vs.110).aspx .PARAMETER InheritanceFlags The flags to set on how you'd like the object inheritance to be set. Possible values are ContainerInherit, None or ObjectInherit. http://msdn.microsoft.com/en-us/library/system.security.accesscontrol.inheritanceflags(v=vs.110).aspx .PARAMETER PropagationFlags The flag that specifies on how you'd permission propagation to behave. Possible values are InheritOnly, None or NoPropagateInherit. http://msdn.microsoft.com/en-us/library/system.security.accesscontrol.propagationflags(v=vs.110).aspx .PARAMETER Type The type (Allow or Deny) of permissions to add. http://msdn.microsoft.com/en-us/library/w4ds5h86(v=vs.110).aspx #> [CmdletBinding()] param ( [Parameter(Mandatory = $true)] [ValidateScript({ Test-Path -Path $_ })] [string]$Path, [Parameter(Mandatory = $true)] [string]$Identity, [Parameter(Mandatory = $true)] [string]$Right, [Parameter(Mandatory = $true)] [string]$InheritanceFlags, [Parameter(Mandatory = $true)] [string]$PropagationFlags, [Parameter(Mandatory = $true)] [string]$Type ) process { try { $Acl = Get-Acl -Path $Path $Ar = New-Object System.Security.AccessControl.FileSystemAccessRule($Identity, $Right, $InheritanceFlags, $PropagationFlags, $Type) $Acl.SetAccessRule($Ar) Set-Acl $Path $Acl } catch { Write-Error -Message "Error: $($_.Exception.Message) - Line Number: $($_.InvocationInfo.ScriptLineNumber)" $false } } } } process { try { ## Create the base home folder path for all users Write-Verbose "Creating the parent folder $BaseHomeFolderPath" if (!(Test-Path -Path $BaseHomeFolderPath -PathType Container)) { mkdir -Path $BaseHomeFolderPath | Out-Null } ## Set NTFS permissions for the base home folder Write-Verbose "Setting NTFS permissions for $BaseHomeFolderPath" $Params = @{ 'Path' = $BaseHomeFolderPath 'Identity' = 'Domain Admins' 'Right' = 'FullControl' 'InheritanceFlags' = 'None' 'PropagationFlags' = 'NoPropagateInherit' 'Type' = 'Allow' } Set-MyFileSystemAcl @Params $Params.Identity = 'Administrators' Set-MyFileSystemAcl @Params $Params.Identity = 'Domain Users' $Params.Right = 'Modify' Set-MyFileSystemAcl @Params ## Disable inheritance and remove all inherited ACEs Write-Verbose "Disabling NTFS inheritance on $BaseHomeFolderPath" $Acl = Get-Acl -Path $BaseHomeFolderPath $Acl.SetAccessRuleProtection($True, $False) Set-Acl -Path $BaseHomeFolderPath -AclObject $Acl ## Create the base home folder share Write-Verbose "Creating the home folder file share $HomeFolderShareName" $WmiShare = [wmiClass] 'Win32_share' $WmiShare.Create($BaseHomeFolderPath, $HomeFolderShareName, 0) | Out-Null ## Set share permissions for the base home folder Write-Verbose "Creating the parent folder share permissions" Grant-SmbShareAccess -Name $HomeFolderShareName -AccountName 'Authenticated Users' -AccessRight Full -Force | Out-Null Revoke-SmbShareAccess -Name $HomeFolderShareName -AccountName 'Everyone' -Force | Out-Null foreach ($User in $UserAccount) { try { ## Figure out the samaccountname if ($User.FirstName.Length -lt 4) { $UserPart1 = $User.FirstName.SubString(0, ($User.FirstName.Length - 1)) } else { $UserPart1 = $User.FirstName.SubString(0, 3) } if ($User.LastName.Length -lt 4) { $UserPart2 = $User.LastName.SubString(0, ($User.LastName.Length - 1)) } else { $UserPart2 = $User.LastName.SubString(0, 3) } $Username = "$UserPart1$UserPart2" ## Create the home folder if it doesn't exist $HomeFolder = "$BaseUncHomeFolderPath\$Username" if (!(Test-Path -Path $HomeFolder)) { Write-Verbose "Creating the folder $HomeFolder" mkdir $HomeFolder | Out-Null } $DomainDn = (Get-AdDomain).DistinguishedName ## Create the user in AD $NewUserParams = @{ 'GivenName' = $User.FirstName 'Path' = "$OuLocation,$DomainDn" 'Surname' = $User.LastName 'Name' = "$($User.FirstName) $($User.LastName)" 'SamAccountName' = $Username 'HomeDirectory' = $HomeFolder 'HomeDrive' = $HomeDrive 'UserPrincipalName' = $Username 'DisplayName' = "$($User.FirstName) $($User.LastName)" 'AccountPassword' = (ConvertTo-SecureString $DefaultUserPassword -AsPlainText -Force) 'Enabled' = $true } Write-Verbose "Creating the AD username $Username" New-AdUser @NewUserParams ## Copy test files to the home folder Copy-Item -Path "$TestFilesFolderPath\*" -Destination $HomeFolder -Recurse -Force ## Set permissions on the home folder $Params = @{ 'Path' = $HomeFolder 'Identity' = $Username 'Right' = 'Modify' 'InheritanceFlags' = 'ContainerInherit,ObjectInherit' 'PropagationFlags' = 'NoPropagateInherit' 'Type' = 'Allow' } Set-MyFileSystemAcl @Params } catch { Write-Error "$($_.Exception.Message) - Line Number: $($_.InvocationInfo.ScriptLineNumber)" } } } catch { Write-Error "$($_.Exception.Message) - Line Number: $($_.InvocationInfo.ScriptLineNumber)" } } |
Now simply run the script and sit back.
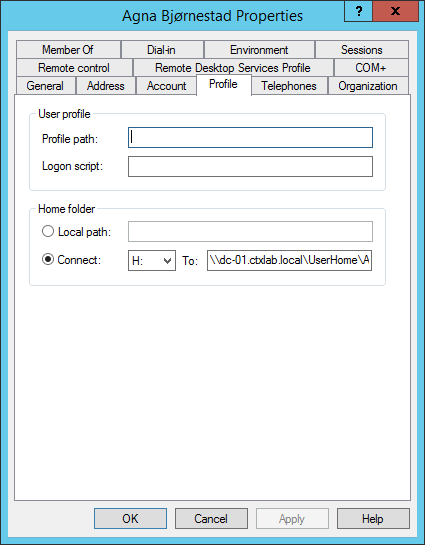
The HomeFolder path is set correctly.
The HomeFolder is created with the right permissions and test data are copied to the root of the HomeDrive.
The Share Permission is set to Authenticated Users.
The Users are create in the Organization Unit we specified in the script. Please note that it has to exist or the script will fail.
Say what? You like the Organization Unit Structure? Well I’ll give you the script for that as well.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 |
<# Created: 2013-12-16 Version: 1.0 Author Mikael Nystrom and Johan Arwidmark Homepage: http://www.deploymentfundamentals.com Disclaimer: This script is provided "AS IS" with no warranties, confers no rights and is not supported by the authors or DeploymentArtist. Author - Mikael Nystrom Twitter: @mikael_nystrom Blog : http://deploymentbunny.com Author - Johan Arwidmark Twitter: @jarwidmark Blog : http://deploymentresearch.com #> $CurrentDomain = Get-ADDomain New-ADOrganizationalUnit -Name:"Deployment" -Path:"$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Users" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"vDesktops" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Workstations" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Security Groups" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Admin Accounts" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Service Accounts" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Servers" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Security Groups" -Path:"OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Infrastructure Servers" -Path:"OU=Servers,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Hyper-V Servers" -Path:"OU=Servers,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Database Servers" -Path:"OU=Servers,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Microsoft" -Path:"OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"Citrix" -Path:"OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"WS08" -Path:"OU=Microsoft,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"WS12" -Path:"OU=Microsoft,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"FMA" -Path:"OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"IMA" -Path:"OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"WS08" -Path:"OU=IMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W10" -Path:"OU=FMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W8" -Path:"OU=FMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W7" -Path:"OU=FMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"WS08" -Path:"OU=FMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"WS12" -Path:"OU=FMA,OU=Citrix,OU=vDesktops,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W7" -Path:"OU=Workstations,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W8" -Path:"OU=Workstations,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator New-ADOrganizationalUnit -Name:"W10" -Path:"OU=Workstations,OU=Deployment,$CurrentDomain" -ProtectedFromAccidentalDeletion:$false -Server:$CurrentDomain.PDCEmulator |






Thank you… Greath script. Line 63 … you’d permission …. ‘ sschuold not be there 🙂
Thanks, please explain, I’m not the guru, that’s why I outsource the complicated PowerShell stuff like this one 🙂
You are a Citrix guru. That’s more than enough:-)